Your Customers’ Data is Your Responsibility: A Guide to Secure & Trustworthy Repairs

Introduction
Imagine handing over your life’s most precious digital belongings—family photos, financial documents, private messages—to a complete stranger. This is the reality for every customer who walks into your repair shop. They are placing a tremendous amount of trust in you, and in an age of data breaches and privacy concerns, their biggest fear is not that you won’t fix their device, but that you won’t protect their data.
For a modern repair shop in Nagpur, Pune, or anywhere else in the world, data security is no longer a niche concern. It’s a foundational pillar of your brand. By making data privacy a central part of your service, you don’t just build trust; you build a reputation as a secure repair shop that customers will gladly pay a premium for.
This isn’t about complex, technical jargon. It’s about a clear, professional blueprint for handling your customers’ most sensitive information with the care it deserves.
The Trust Blueprint: A Step-by-Step Guide
Here is a practical, actionable guide to turning data security into your greatest competitive advantage.
Step 1: The Trust Pact: Communicate & Get Consent
Transparency is the first step to building trust. Before you touch a single device, you must have a clear, written policy.
-
Get a Digital Signature: Don’t just rely on a verbal agreement. Have the customer sign a digital work authorization that includes a clear privacy clause. This should state that you will only access the data necessary for the repair and that all personal information will be handled with the utmost confidentiality.
-
Be a Guardian, Not a Browser: Make it a strict policy that technicians are only allowed to access the files and functions of a device that are essential for the repair. No browsing photos, checking emails, or opening social media accounts. Ever.
Step 2: Secure Handling & Data Recovery
A customer may come in for a simple screen repair, but what if the repair fails and they lose their data? Offering a professional data recovery services and a clear data backup policy will save you from a major liability.
-
Backup, Backup, Backup: Before starting a repair, perform a secure data backup of the customer’s device if they’ve requested it. Use a professional tool and a separate, encrypted storage device. Never back up a customer’s data to a general-purpose computer or external hard drive.
-
Use Secure Notes: Your
repair softwareshould have a secure notes feature on every work order. This is where you can document the customer’s login details, but it must be in a secure, encrypted part of the system that is only accessible to authorized technicians. Never write down passwords on a sticky note.
Step 3: The Professional Workflow
A professional workflow is a secure workflow. The process of the repair itself must reinforce your commitment to security.
-
Clear Workspaces: Designate a clean, organized, and private workspace for each repair. This prevents accidental data leaks or unauthorized viewing of sensitive information.
-
Access Control: Not every employee needs access to every part of your system. Your
BytePhasesoftware should have role-based permissions, ensuring that only senior technicians or managers can access sensitive customer notes or data backups. -
Final Data Sanitation: After the repair is complete and the device has been returned to the customer, you must securely erase any temporary files or data that were created during the repair.
Step 4: The Final Hand-Off
The final moments of the transaction are just as important as the first. A secure and professional hand-off can be the difference between a satisfied customer and a loyal one.
-
Confirm Security: When returning the device, take a moment to reassure the customer that their data was not accessed beyond what was necessary for the repair and that it has been handled with the highest level of care.
-
The Right Tools: A
pos systemthat can provide a detailed, itemized invoice with a clear privacy statement is a simple way to reinforce your commitment. It’s a small detail that can have a big impact on a customer’s perception of your professionalism.
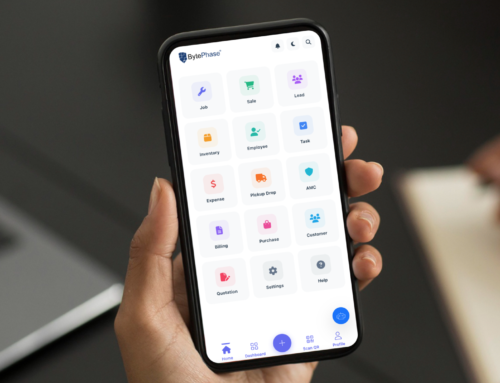
The BytePhase Advantage: The Platform for Trust
Building a secure and trustworthy repair business is nearly impossible to do manually. You need a system that enforces your policies and provides a transparent workflow. That’s where BytePhase comes in.
Our platform is designed to be the backbone of a professional, secure repair shop.
-
Digital Consent & Work Orders: Our system allows you to create customizable work orders that include your data privacy agreement and require a digital signature from the customer, providing an auditable record for every repair.
-
Secure & Encrypted Notes: Our secure notes feature ensures that sensitive customer information is never stored in plain text or on a physical piece of paper.
-
Audit Trails: BytePhase provides a clear history of every action taken on a repair ticket, so you know exactly who accessed what and when, ensuring accountability and peace of mind.
In a competitive market, a commitment to your customers’ data security is not just a policy; it’s a promise. By implementing a secure and professional workflow, you transform your business from a simple computer service and repair shop into a trusted partner, and that is a brand that will stand the test of time.